OS Name/Version: Debian 12
Product Name/Version: AMP Release “Decadeus” v2.4.8, built 29/01/2024 18:40
Problem Description:
I’m running into an issue where AMP is grabbing a user attribute that is either incorrect or nonexistent and causing NullReference exceptions, or Insufficient Access
Steps to reproduce:
- Step 1 - Set up Authentik
- Step 2 - Configured Authentik to sync users with my Active Directory Server.
- Step 3 - Followed Cooptonian’s YouTube guide to create a generic LDAP provider/outpost
- Step 4 - Configure LDAP settings in AMP per the KB
- Step 5 - Assign an AMP_ group in Authentik to a user. AD synced, or from Authentik’s local DB.
- Step 6 - Insufficient access error if logging in with AD synced user, NullReference exception if logging in with a local Authentik account.
Actions taken to resolve so far:
Authentik’s domain is ldap.goauthentik.io its IP is 10.2.1.3
My LDAP domain that Authentik syncs with is zebra.local
Authentik relies on the dn attribute, and from what I can tell, AMP is trying to use the distinguishedName attribute that exists on my LDAP domain controller.
Here is my LDAP configuration in AMPConfig.conf
################################
# Login
################################
Login.UseAuthServer=False
# Login.AuthServerURL - The URL for the ADS instance providing authentication when using UseAuthServer
Login.AuthServerURL=http://localhost:8080/
Login.MetricsServerPort=12820
Login.UseLDAPLogins=True
Login.UseLDAP3=True
Login.AllowLocalUsersWithLDAP=True
Login.LDAPAuthDomain=ldap.goauthentik.io/DC=ldap,DC=goauthentik,DC=io
Login.LDAP3Host=ldap.goauthentik.io
Login.LDAP3FilterDN=OU=users,DC=ldap,DC=goauthentik,DC=io
Login.LDAP3UserDN=cn=ldapservice,ou=users,dc=ldap,dc=goauthentik,dc=io
Login.LDAPGroupPrefix=AMP_
Login.LDAPUserDomain=ldap.goauthentik.io
Login.LDAP3UsesSSL=False
Login.LDAPADPre2000=False
Login.LDAPStripDomainFromFilter=True
Login.LDAPQueryUsername=cn=ldapservice,ou=users,dc=ldap,dc=goauthentik,dc-io
Login.LDAPQueryPassword=[redacted]
################################
The below code shows my LDAP user having both a dn: attribute and distinguishedName attribute. dn is Authentik, distinguishedName is carried over from the Active Directory server that Authentik syncs with.
$ ldapsearch -x -H ldap://10.2.1.3 -D "cn=zebra,ou=users,dc=ldap,dc=goauthentik,dc=io" -b 'ou=users,DC=ldap,DC=goauthentik,DC=io' 'cn=zebra' -W
# LDAPv3
# base <ou=users,DC=ldap,DC=goauthentik,DC=io> with scope subtree
# filter: cn=zebra
# requesting: ALL
#
# zebra, users, ldap.goauthentik.io
dn: cn=zebra,ou=users,dc=ldap,dc=goauthentik,dc=io
distinguishedName: CN=Zebra,OU=home-users,DC=zebra,DC=local
sn:
upn: zebra@zebra.local
givenName: Zebra
ldap_uniq: [redacted]
mail: [redacted]
uidNumber: 2007
memberOf: cn=AMP_Users,ou=groups,dc=ldap,dc=goauthentik,dc=io
memberOf: cn=G-HomeAdmins,ou=groups,dc=ldap,dc=goauthentik,dc=io
memberOf: [redacted irrelevant groups]
cn: zebra
displayName: Zebra
uid: ca785f88c751a72b126ad845dc750f5df7c7cb5ee95759808326ca35b59bc75e
name: Zebra
gidNumber: 2007
ak-superuser: TRUE
homeDirectory: /home/zebra
ak-active: TRUE
sAMAccountName: zebra
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: user
objectClass: posixAccount
objectClass: goauthentik.io/ldap/user
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Now, watch what happens when I try to log into AMP with my AD username. Notice on line 2 that AMP is reading the distinguishedName attribute which is carried over from AD, seen on line 8 of the previous code snippet.
[05:12:16] [LDAPDSAuth Debug] : LDAP query filter: (&(objectClass=user)(sAMAccountName=zebra))
[05:12:16] [LDAPDSAuth Debug] : LDAP user search path: LDAP://ldap.goauthentik.io/CN=Zebra,OU=home-users,DC=zebra,DC=local
[05:12:16] [LDAPDSAuth Debug] : LDAP auth user: zebra@ldap.goauthentik.io
[05:12:16] [Core Debug] : LdapException
[05:12:16] [Core Debug] : [0] (LdapException) : Insufficient Access Rights
[05:12:16] [Core Debug] : at DirectoryServices.DirectoryEntry.InitBlock ()
at DirectoryServices.DirectoryEntry.get_conn ()
at DirectoryServices.DirectoryEntry.LoadProperties (DirectoryServices.PropertyCollection properties, String[] propertyNames)
at DirectoryServices.DirectoryEntry.RefreshCache ()
at (wrapper remoting-invoke-with-check) DirectoryServices.DirectoryEntry.RefreshCache()
at GSMyAdmin.Authentication.LDAPDSAuth.Authenticate (String username, String password)
[05:12:16] [LDAPDSAuth Info] : The LDAP query was successful but the user credentials were refused.
[05:12:16] [Auth Debug] : LDAP Login failure for zebra: The query was successful but the user credentials were refused.
[05:12:16] [Core Debug] : Login failed for zebra - Failure : LDAP failure - check logs -
Because the DC and OU in the distinguishedName attribute does not exist in Authentik, logging in fails because that DN has insufficient access. I was able to prove this by mimicking the search in ldapsearch:
The following command returns my LDAP user, shown in the second code snippet from the top.
Note: these queries were run using the IP address to rule out DNS being an issue. I tested using the FQDN and got the same results.
$ ldapsearch -x -H ldap://10.2.1.3 -D "cn=zebra,ou=users,dc=ldap,dc=goauthentik,dc=io" -b 'ou=users,DC=ldap,DC=goauthentik,DC=io' 'cn=zebra' -W
When using the same ldapsearch query with the bind DN matching what AMP queries with, I get an Insufficient Access error. Specifically, ldap_bind: Insufficient access (50)
$ ldapsearch -x -H ldap://10.2.1.3 -D "CN=Zebra,OU=home-users,DC=zebra,DC=local" -b 'ou=users,DC=ldap,DC=goauthentik,DC=io' 'cn=zebra' -W
When following the same steps using an Authentik-based account, not synced from my local Active Directory, I am presented with a NullReference Exception.
I created a dummy account to test with, ICanHazCheesburgr and ran the same LDAP searches
When using ldapsearch -x -H ldap://10.2.1.3 -D "cn=icanhazcheesburgr,ou=users,dc=ldap,dc=goauthentik,dc=io" -b 'ou=users,DC=ldap,DC=goauthentik,DC=io' 'cn=icanhazcheesburgr' -W
It successfully returned LDAP information. Notice this user has a dn attribute on line 10, but no distinguishedName attribute
# extended LDIF
#
# LDAPv3
# base <ou=users,DC=ldap,DC=goauthentik,DC=io> with scope subtree
# filter: cn=icanhazcheesburgr
# requesting: ALL
#
# IcanHazCheesburgr, users, ldap.goauthentik.io
dn: cn=IcanHazCheesburgr,ou=users,dc=ldap,dc=goauthentik,dc=io
memberOf: cn=AMP_Users,ou=groups,dc=ldap,dc=goauthentik,dc=io
cn: IcanHazCheesburgr
name: IcanHazCheesburgr
displayName: IcanHazCheesburgr
mail: no@where.com
homeDirectory: /home/IcanHazCheesburgr
ak-superuser: FALSE
sAMAccountName: IcanHazCheesburgr
uid: 90d08125126e2224a7c5abc29b1c78ed1fac36f6b80d4efc61ebd67bcb2d6e81
ak-active: TRUE
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: user
objectClass: posixAccount
objectClass: goauthentik.io/ldap/user
uidNumber: 2027
gidNumber: 2027
sn: IcanHazCheesburgr
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
If I manually specify a distinguishedName in Authentik’s attribute editor, I am presented with the same error message that my LDAP user gets:
[20:16:39] [LDAPDSAuth Debug] : LDAP query filter: (&(objectClass=user)(sAMAccountName=IcanHazCheesburgr))
[20:16:39] [LDAPDSAuth Debug] : LDAP user search path: LDAP://ldap.goauthentik.io/cn=IcanHazCheesburgr,ou=users,dc=ldap,dc=goauthentik,dc=io
[20:16:39] [LDAPDSAuth Debug] : LDAP auth user: IcanHazCheesburgr@ldap.goauthentik.io
[20:16:39] [Core Debug] : LdapException
[20:16:39] [Core Debug] : [0] (LdapException) : Insufficient Access Rights
[20:16:39] [Core Debug] : at DirectoryServices.DirectoryEntry.InitBlock ()
at DirectoryServices.DirectoryEntry.get_conn ()
at DirectoryServices.DirectoryEntry.LoadProperties (DirectoryServices.PropertyCollection properties, String[] propertyNames)
at DirectoryServices.DirectoryEntry.RefreshCache ()
at (wrapper remoting-invoke-with-check) DirectoryServices.DirectoryEntry.RefreshCache()
at GSMyAdmin.Authentication.LDAPDSAuth.Authenticate (String username, String password)
[20:16:39] [LDAPDSAuth Info] : The LDAP query was successful but the user credentials were refused.
[20:16:39] [Auth Debug] : LDAP Login failure for IcanHazCheesburgr: The query was successful but the user credentials were refused.
[20:16:39] [Core Debug] : Login failed for IcanHazCheesburgr - Failure : LDAP failure - check logs -
Reposted to comply with the posting rules
Edit:
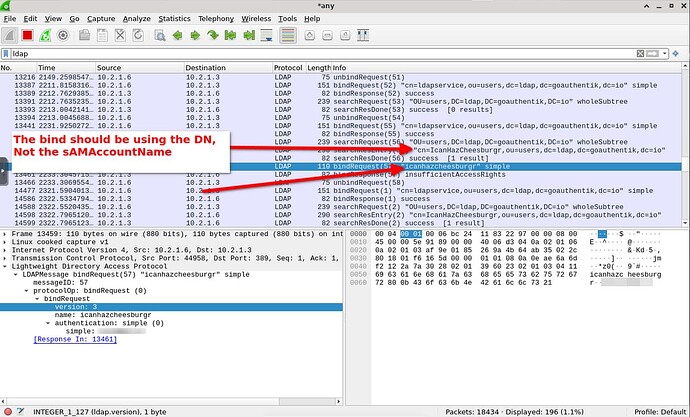
I did some more digging using WireShark.
AMP is not passing the correct user DN to the ldap server which causes authentication to fail.
For example, if I log into ICanHazCheesburgr, ldapsearch binds to the LDAP server and returns 3 attributes, sAMAccountName, distinguishedName, and memberOf.
If any of those 3 do not exist, it throws a NullReference exception.
If they DO exist, AMP will then try to bind to the same ldap server using only the sAMAccountName.
This isn’t enough, and causes LDAP to return with error 50, insufficient access rights, since it is trying to bind only using the sAMAccountName, not the full bind DN.
it is authenticating with IcanHazCheesburgr, instead of cn=IcanHazCheesburgr,ou=users,dc=ldap,dc=goauthentik,dc=io
I can’t tell if this is a bug or misconfiguration on my end, but I would really appreciate a response.
I looked everywhere on this forum to find out what “Priority Support” response times are, but the license I paid for includes it. Hoping to be clued in on what to expect for support response times. Thanks.