We have a company running security scans for us.
I happen to run an AMP server on the scanned network.
Every time, the security report is reporting the AMP instance:
443/tcp www: Info leak (backup-/config files)
8080/tcp www: Info leak (backup-/config files)
and
2223/tcp ssh Weak SSH kryptering
I run a single instance on this server; a Valheim server, with this network port status:
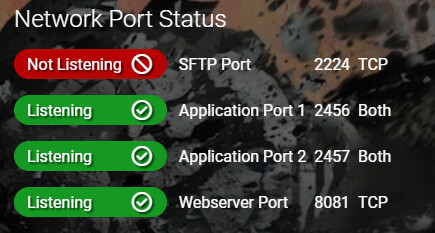
Doesn’t seem that that instance is even using port 2223, so where is this coming from?
And why is port 8080 open?
I can reach the AMP server on both http://amp.domain.tld:8080 and https://amp.domain.tld
What can be done to please the Security Scanner?
The server is running on a Ubuntu Linux server
Thanks